Statement
An employee has lost his Keepass password. He couldn’t remember it, and couldn’t find his password file. After hours of searching, it turns out that he has sent a screen of his passwords to one of his colleagues, but it’s still nowhere to be found.
He’s asking for your help to find him.
It’s up to you
sha256sum: 028c8561f087da873b08968d55141dcfc8f10a47e787f79c35b2da611a5e07ce
We are provided with two files for this challenge: a PNG image and a KeePass database file. To access the database, you’ll need to download KeePass—a popular password manager. The goal is to retrieve the flag, which is stored within the database. To do that, we first need to determine the correct master password.
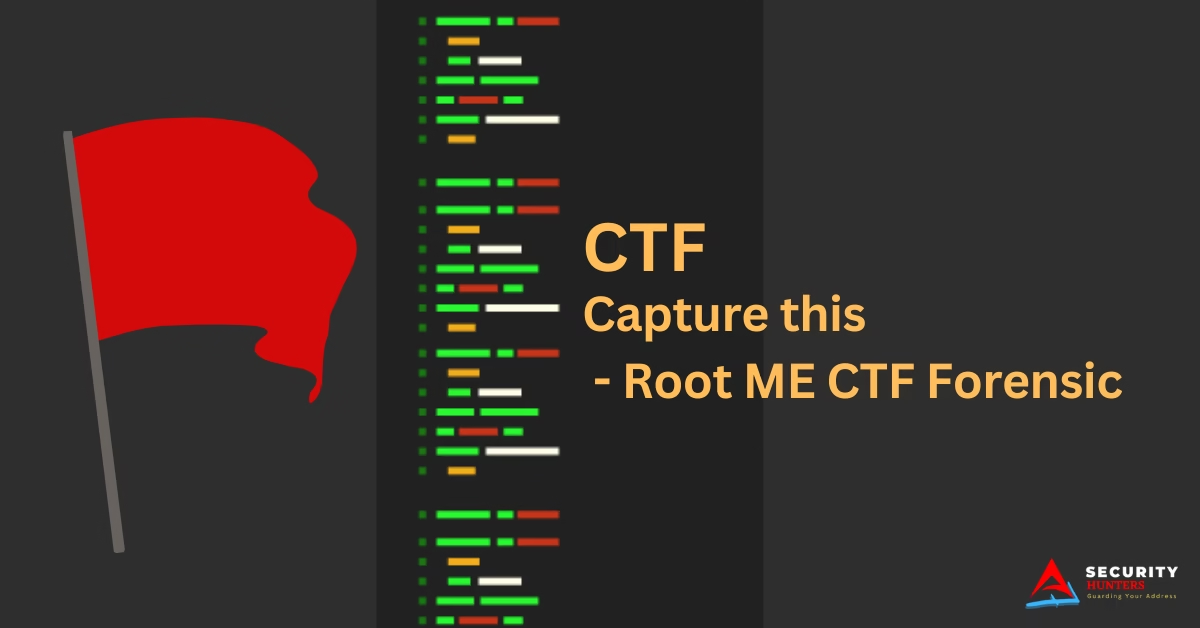
Let’s start by examining the image file. It’s a screenshot of an Excel spreadsheet containing multiple passwords. While it might be tempting to assume one of these passwords is the master key, that’s not the case. Similarly, trying to extract the password using metadata analysis or file carving tools like Foremost is a red herring and won’t lead you to the solution.
Upon closely examining the image, you can spot the letter “k” peeking out on the far right side of the Excel spreadsheet. This might hint at the word “KeePass”, suggesting that the master key could be present further to the right in the spreadsheet. However, since the image is cropped, we can’t see beyond that point. So the question becomes: How can we “uncrop” the image to reveal the rest of the content?
If you look at the bottom taskbar in the screenshot, you’ll notice only two applications are open: Excel and the Snipping Tool. This is a critical clue.
Table of Contents
ToggleEnter aCropalypse (CVE-2023-28303)
Discovered in early 2023, aCropalypse is a vulnerability affecting image editing tools on Google Pixel phones and Windows 10/11 Snipping Tool. The flaw allowed cropped images to retain the original uncropped data.
This occurred because the software failed to properly truncate the file after editing. As a result, residual image data from the original screenshot was left behind in the saved file.
What Does This Mean?
Even if an image appears cropped or redacted (e.g., a portion of the image is blacked out or hidden), the full original image might still be recoverable. This extra data isn’t visible in standard image viewers, which typically stop reading the file after reaching the first end-of-file marker. However, this residual data can be extracted using specialized tools.
A helpful sign that an image may be vulnerable is if its file size appears unusually large for a cropped screenshot—indicating leftover data might still exist.
Recovery Tools
There are several tools available to test and exploit this vulnerability:
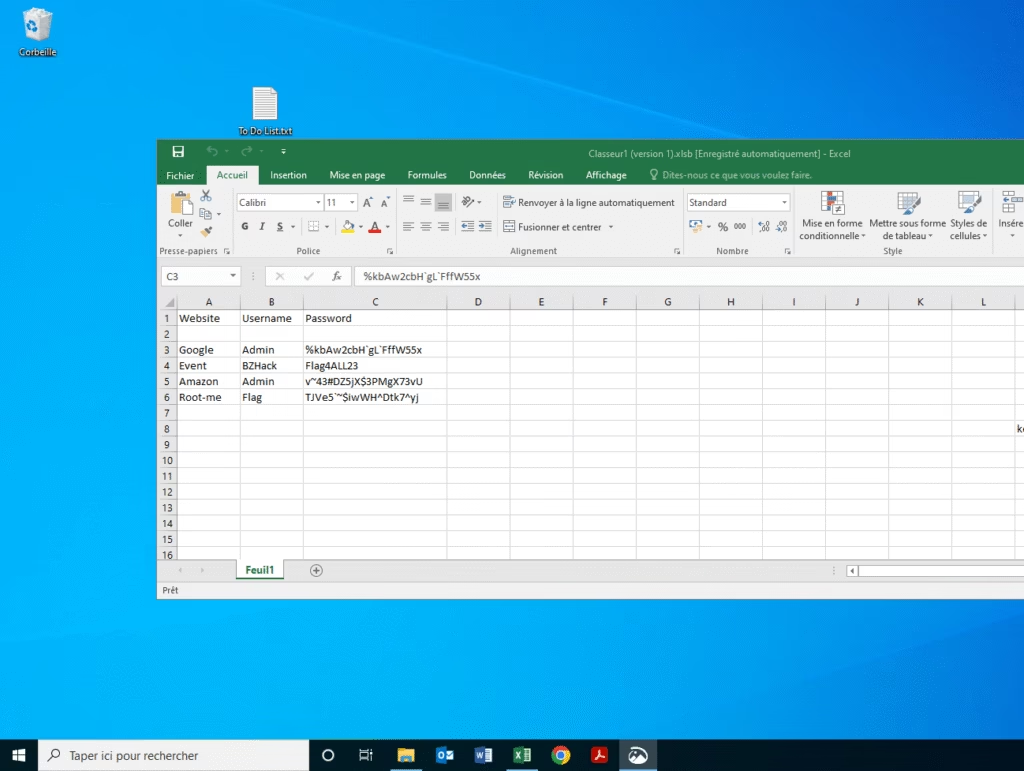
- aCropalypse Detector: https://lordofpipes.github.io/acropadetect/
- Screenshot Recovery Tool: https://acropalypse.app/
- Python-based GUI Recovery Tool by Frank Webber and Philipp Ensinger: https://github.com/frankthetank-music/Acropalypse-Multi-Tool
By using these tools, it may be possible to recover the full screenshot—including the hidden part of the spreadsheet—which could potentially contain the master password for the KeePass database.
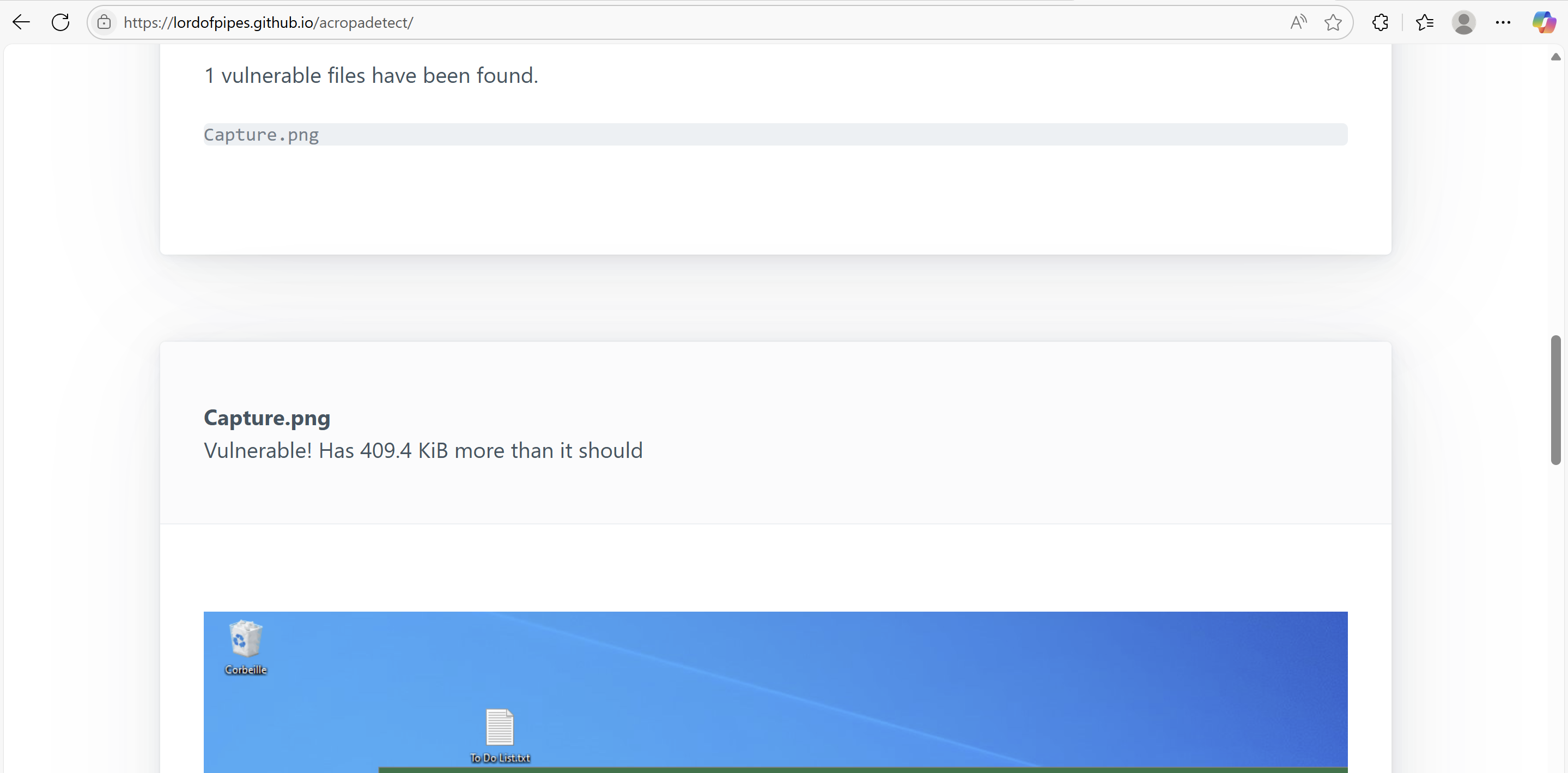
When attempting to recover the image using acropalypse.app, the result turned out to be extremely noisy and practically unreadable. While it confirmed the presence of residual data, it wasn’t sufficient for extracting useful information.
Better Results with the GitHub GUI Tool
The best results came from the Acropalypse Multi-Tool GUI, available on GitHub:
🔗 https://github.com/frankthetank-music/Acropalypse-Multi-Tool
sudo apt updat && upgrade
git clone https://github.com/frankthetank-music/Acropalypse-Multi-Tool
python3 -m venv acropalypse-env
source acropalypse-env/bin/activate
pip install Pillow sv_ttk
python gui.py
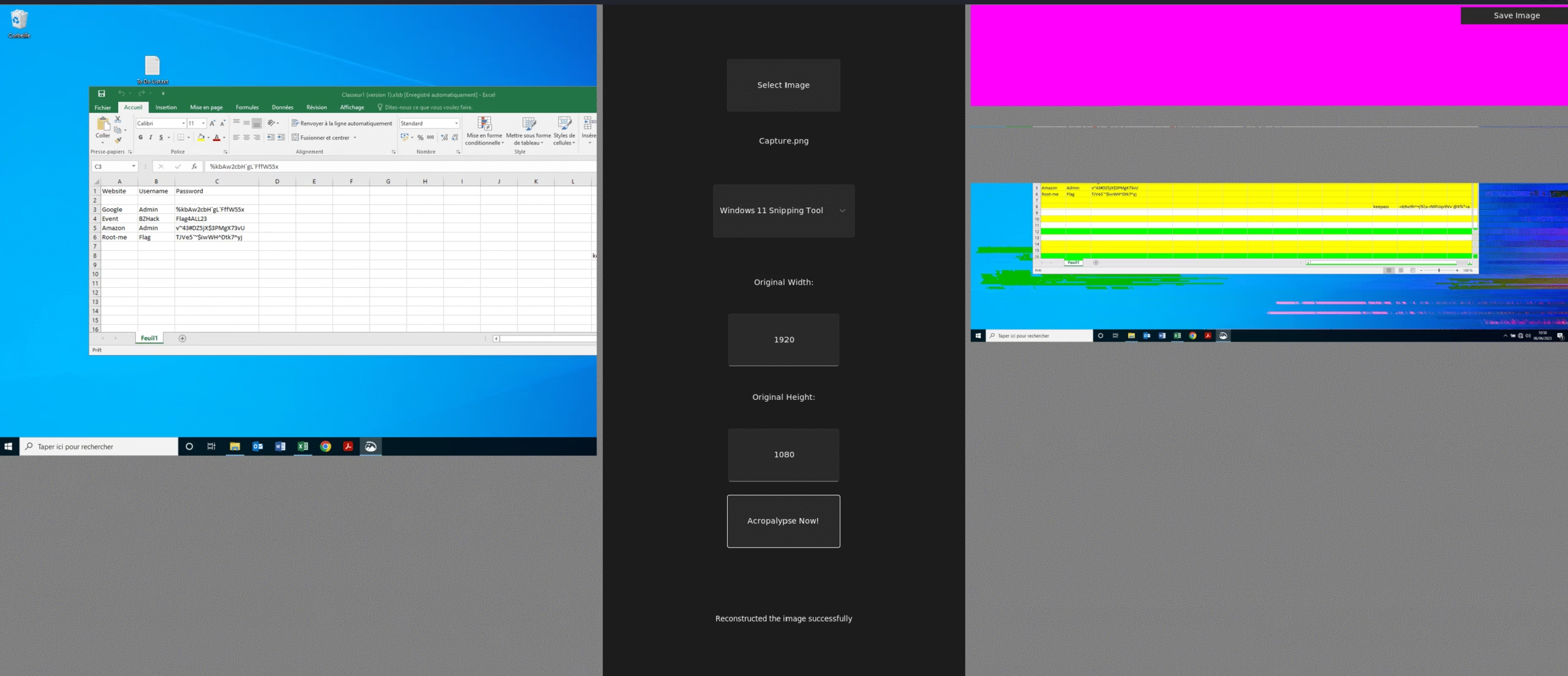
We get the restored image as output where we can clearly see the keypass password- “-=b9w9h^+j%\x-rMPUqv9Vv`@X%*=a”
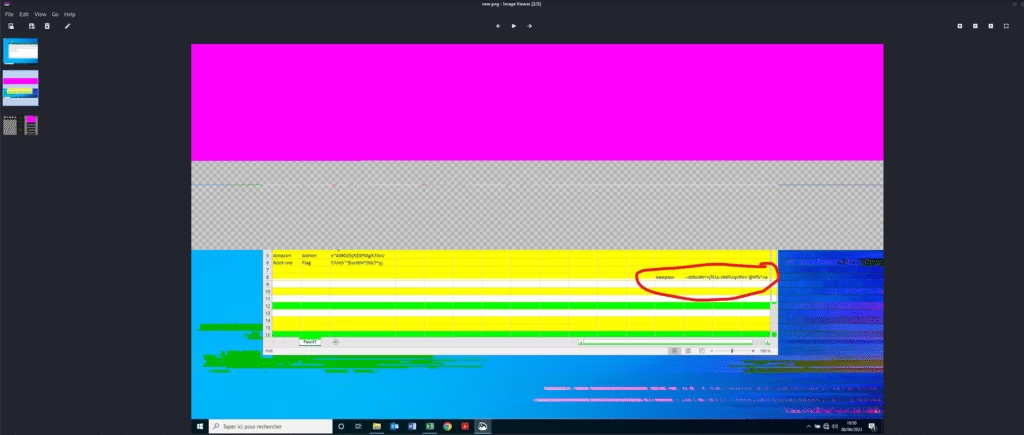
capture-this-ctf-write-up-root-me
This password is the master password for keypass database just make sure to carefully type it. ( there is difference between ` and ‘ )
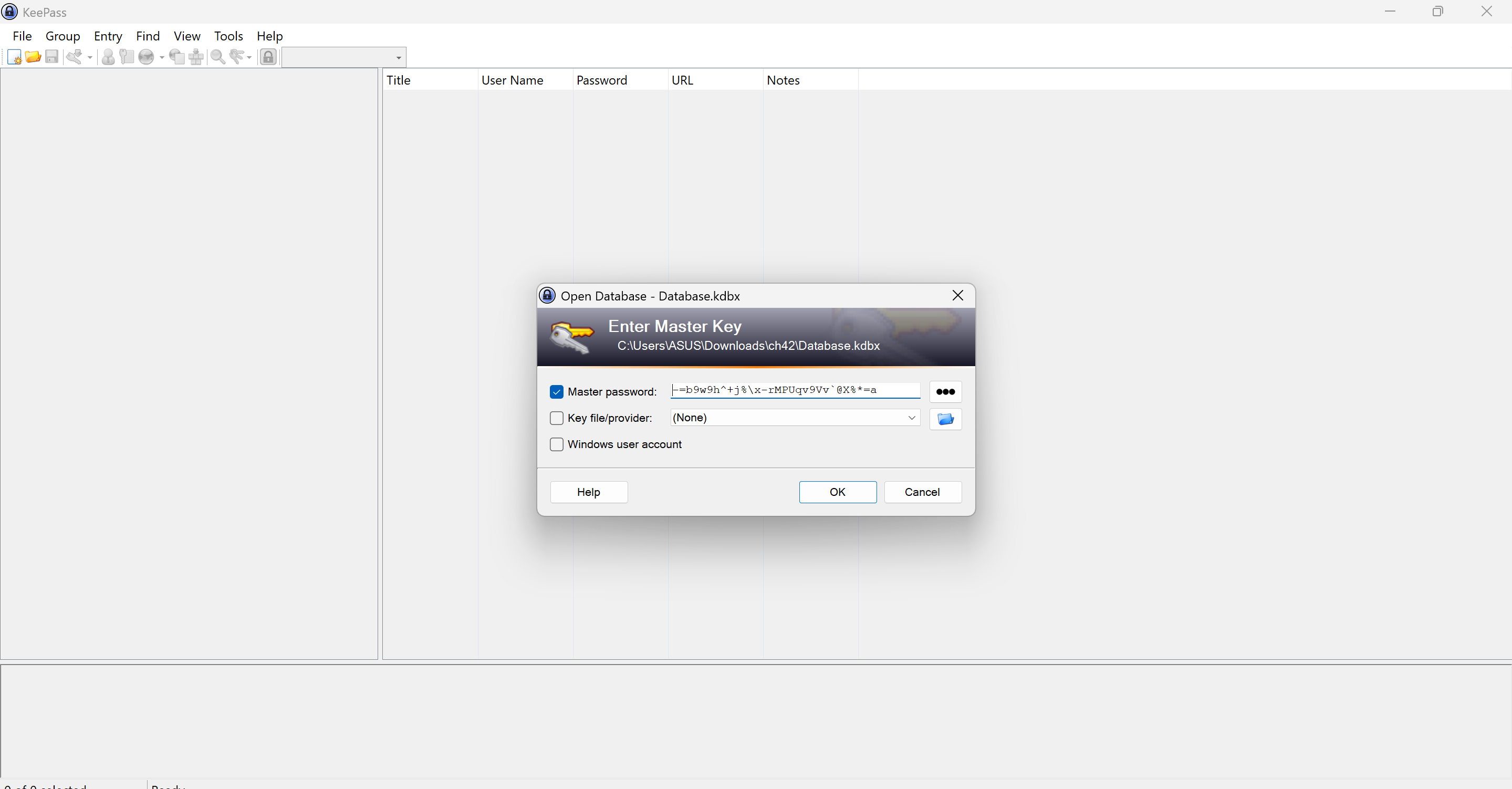
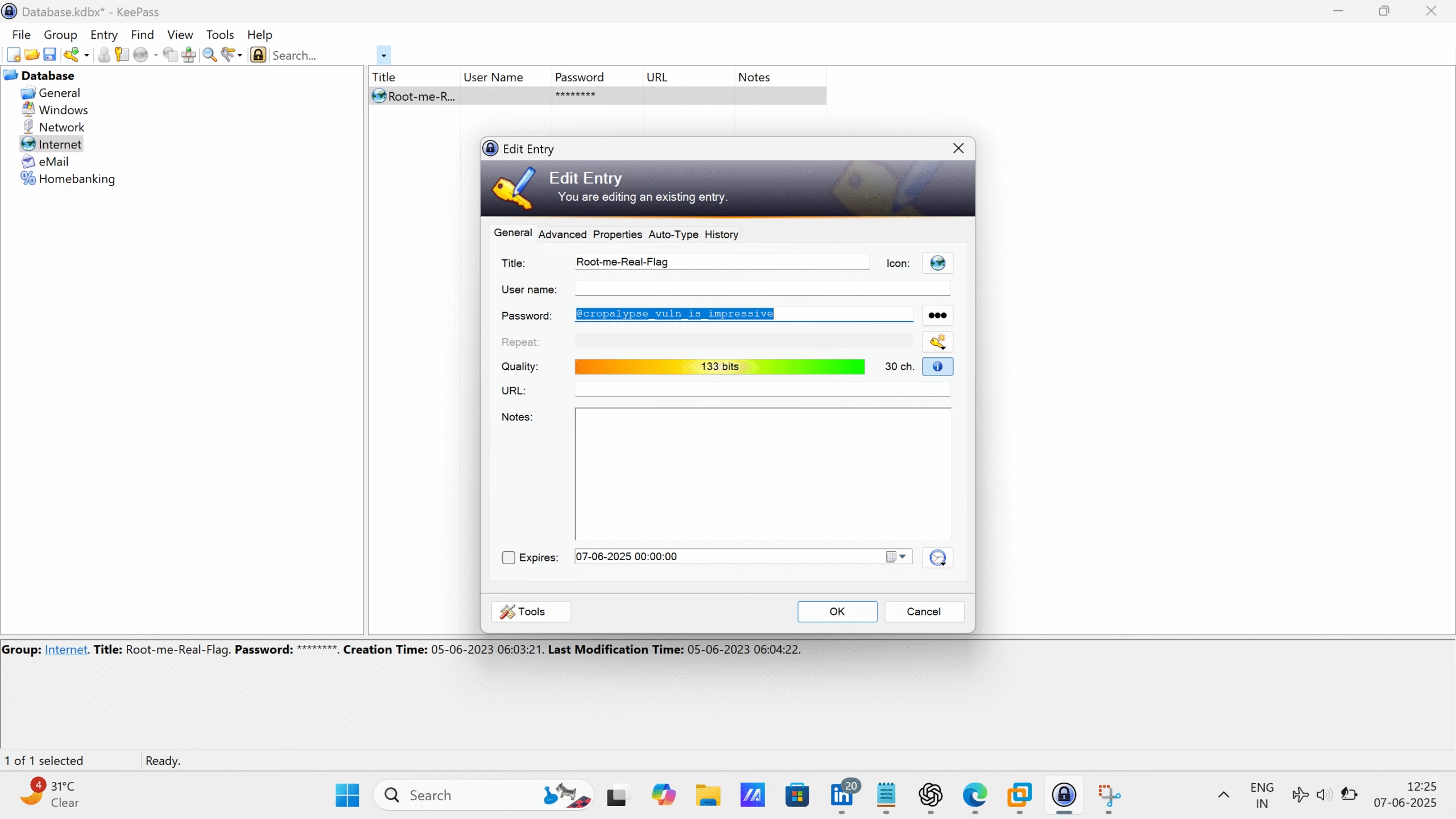
Thus we get the flag for challenge , “@cropalypse_vuln_is_impressive”.
DCFI is a specialized certification focused on digital crime investigation techniques. It equips learners with practical skills in forensic data recovery, analysis, and evidence handling.